Mobile Device Security
Many of our posts have been about IT security, focusing on PCs and laptops. However, with the rapidly changing technology and portability of mobile devices, it is time to focus on mobile device security.
With recent global health events resulting in a surprise shift to either a wholly remote or hybrid remote workforce for many organizations, the need to leverage mobile devices as work endpoints has grown significantly. The Third Annual Ponemon Institute Study on the State of Endpoint Security Risk, sponsored by Morphisec, found that 68% IT security professionals say their company experienced one or more endpoint attacks that compromised data assets or IT infrastructure in 2019, an increase from 54% of respondents in 2017.
How many of your employees are conducting work on their mobile devices? Do they book appointments, share files, text, and even enter their work hours? Perhaps some may do their personal banking on their phones or tablets. All this activity reinforces the need for their mobile device security.
Are the devices they use corporate-owned, allowing you control over what is and is not allowable use, or are they using their personal devices of which you have no control?
What To Look Out For
Unfortunately, phones and tablets are as vulnerable to online threats as PCs and laptops. Due to their portability, they are also objects of physical attacks. Some of the attacks to be on the lookout for include phishing (see our recent blog regarding this type of attack), spyware, unauthorized access, and theft.
Best Practices for Mobile Device Security
Most of these practices will probably sound familiar, but it is still essential to implement them on all mobile devices you and your employees use.
- Passwords – just like for desktop and laptop devices, passwords need to be strong. Try using short phrases such as “I10vemybe$tfriend” (I love my best friend) or “tod@yisa10velyday” (today is a lovely day). Be creative and use a mix of capital and lower-case letters as well as numbers and special characters.” Keep in mind a huge red flag to your security is to use the same password for all your accounts.
- Public WiFi – turn off wireless connectivity when you are not using your phone or tablet. In addition to strengthening your mobile device security, it will also extend the device’s battery life.
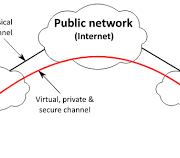
- VPN – a Virtual Private Network (VPN) enables you to connect to a network securely. Connecting in this manner is especially important when traveling and using a hotel or other free network, but it can also deter hackers in your area.
- Antivirus – antivirus applications identify malicious code that could expose your data to hackers. Some antivirus applications include the ability to track and block unknown callers, identify unsafe applications, clear your browsing history, and delete cookies.
- Encryption – is the process of making data unreadable and is a must in today’s world on mobile devices as well as desktops and laptops. Most mobile devices already include built-in encryption. To activate the encryption, all you need to do is locate this feature and enter a password to encrypt your device.
- Backups – if you have ever lost data, you already understand the importance of conducting regular backups on a fixed schedule. No matter how strong your mobile device security is, it’s not foolproof. Backups can get you out of a jam when necessary.
- Updates – as malware and viruses change, your mobile device security may not be able to defend against these new attacks unless it is updated regularly. Most updates offered by the manufacturers as part of their ongoing support include security updates. Samsung will support a device for up to four years, Apple will do it for five to six years, and Google supports its Pixel phones for three years. If your device is older, the carrier may not be supporting it any longer.
Hidden Security Threats
You may be surprised to learn that applications included on your phone may not be secure. In fact, your mobile phone account itself may not be safe if you haven’t set a strong password. Hackers may open accounts with other carriers or add lines to your established account without your knowledge, creating surprise charges for which you could be responsible.
Although extremely advantageous, turning on autofill can leave your device unsecured if it should fall into the wrong hands. You should also get in the habit of always logging out of an account rather than merely closing it with the “X.”
If you need help with any of these suggestions for strengthening your mobile device security, give us a call. We are here to help.